Information Security Risks
Identify and manage information security risks effectively. Assess threats, allocate resources to the most significant risks, and ensure your organisation’s cybersecurity with the Granite Information Security Risks tool.
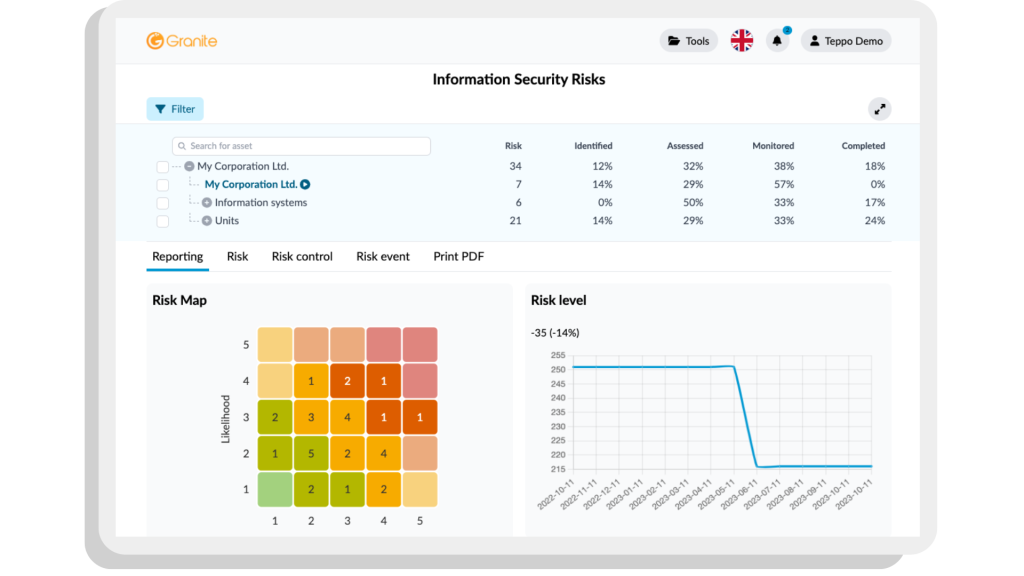
Information Security Risks – what is it about?
Information security risks are threats that can compromise the confidentiality, integrity, and availability of an organisation’s data. Managing these risks is a fundamental part of cybersecurity and ensuring business continuity. The goal is to understand the threats and vulnerabilities present in the organisation’s operations and to define and implement measures that reduce the impact of these risks.
Clear Overview of Information Security Risks
The Granite Information Security Risks tool is designed to support organisations in managing cybersecurity. It provides a clear overview of the state of information security, including threats, vulnerabilities, and controls, and helps direct resources towards the most significant risks.
Proactive risk management
The tool is compatible with widely recognised standards such as ISO 27001, NIST, and NIS2, enabling proactive and continuous improvement in information security risk management.
With the Granite Information Security Risks tool, organisations can effectively manage and monitor information security threats, improve cybersecurity management, and protect their business against the constantly evolving security challenges of today. The tool provides a clear, proactive, and systematic approach to managing information security risks.
Key elements of Information Security Risks

Risk Identification and Assessment
Identify your organisation's information security risks and assess their impact on business operations.

Comprehensive Overview
Create an up-to-date view of cybersecurity threats and vulnerabilities, ensuring an adequate level of security.

Compliance with Standards
Integrate information security risk management into your organisation’s cybersecurity management system, ensuring compliance and continuous improvement in information security.

Management of Mitigation Measures
Define and monitor the implementation of measures to reduce the impact of risks, ensuring cybersecurity remains under control.

Monitoring and Reporting
Track the progress of risk management measures and systematically report on the development of the information security situation through automated reporting.

Clear Entity
Extend usage to include low-threshold reporting of security and data protection incidents and management of audit plans.
Book a call with our experts
We can do a short demo, set up a free trial, or simply discuss your needs.


