Report and manage information security and data protection incidents effectively across your organisation. Create a clear process for reporting, handling, and implementing corrective actions with the Granite Information Security and Data Protection Incidents tool.
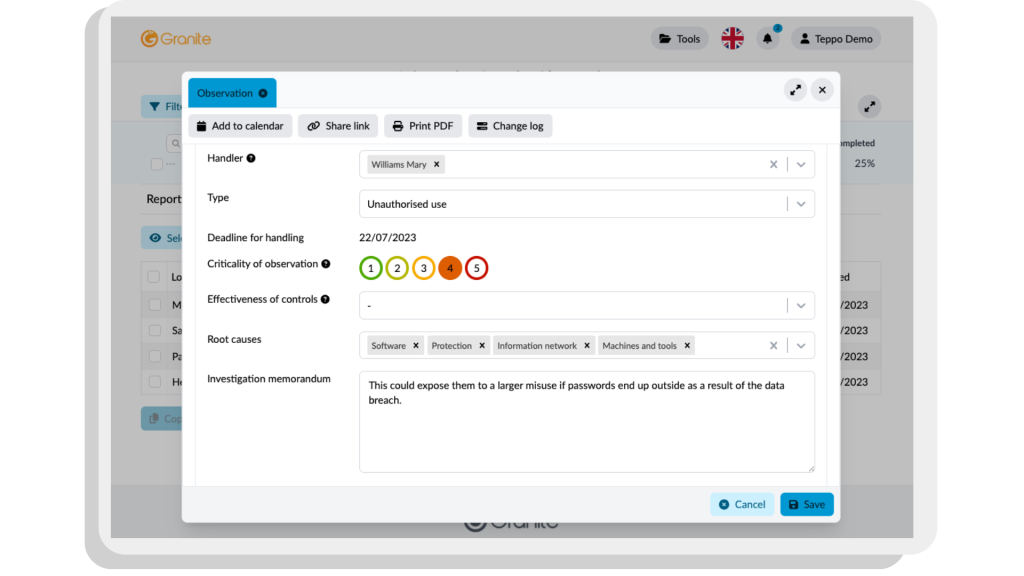
Information security and data protection incidents occur when the organisation’s security or data protection standards or regulations are violated, potentially leading to data-related risks or damage. Managing these incidents is a crucial part of maintaining and developing the organisation’s information security. This process ensures that all security-related observations are handled and documented appropriately. Incident management processes help organisations meet data protection guidelines and demonstrate compliance, which reduces security risks and improves the organisation’s ability to protect its data effectively.
The Granite Information Security and Data Protection Incidents tool is designed to support organisations in managing security and data protection risks.
This tool allows for low-threshold reporting of incidents, documents their handling according to data protection authority guidelines, and supports the implementation of corrective actions.
With this tool, organisations can enhance security levels, manage risks, and ensure business continuity in all situations.
The Granite Information Security and Data Protection Incidents tool enables organisations to effectively manage incidents related to information security and data protection. It supports the development of information security and allows the entire organisation to participate in improving the security culture by ensuring that incidents are handled correctly, and that the organisation’s security level is continuously enhanced.

Enables the entire staff to easily and quickly report information security and data protection incidents.

Gather information on security improvement areas, assess the impact of detected incidents, and manage risks proactively.

Determine the organisation's security level and related threats to ensure business continuity in all circumstances.

Systematically manage and document incidents, ensuring continuous improvement of information security.

Document incident handling, investigation, and corrective actions, ensuring transparency and evidence-based decision-making.

Expand usage to include security risk management and the maintenance and execution of audit plans.
We can do a short demo, set up a free trial, or simply discuss your needs.
