Information Security Risks
Identify and manage information security risks effectively. Assess threats, allocate resources to the most significant risks, and ensure your organisation’s cybersecurity with the Granite Information Security Risks tool.
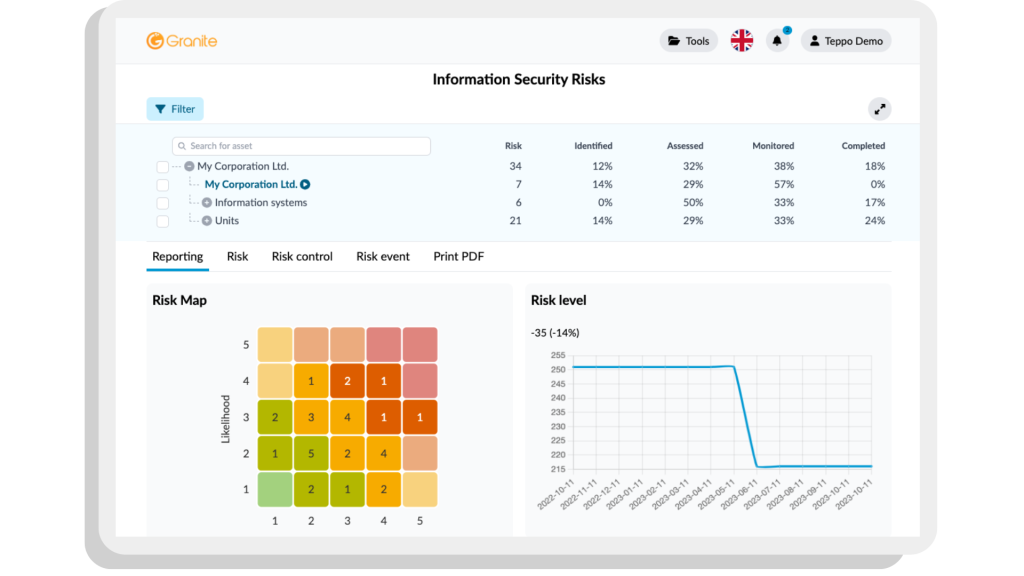
What you need to know about Information Security Risks
Information security risks are threats that can compromise the confidentiality, integrity and availability of your organisation’s data. Managing these risks is fundamental to ensuring your business continuity and cyber security. Understanding vulnerabilities in your operations can help you define and implement measures that reduce the impact of information security risks.
Maximise insights
Granite’s Information Security Risks tool is designed to support your organisation’s cyber security management. With a clear overview of the state of your information security, including threats, vulnerabilities and controls, you can easily direct resources towards the most significant risks.
Proactive risk management
ISO 27001, NIST and NIS2 are not a problem, since Granite’s tool is fully compatible, enabling continuous improvement in information security risk management.
Granite’s Information Security Risks tool can help you manage and monitor your information security threats, improve cybersecurity management and protect your business from the constantly evolving challenges of today. The tool provides a clear, proactive and systematic approach to gaining control of your information security risks.
Key elements of Information Security Risks

Identify and Assess Risk
Know your organisation’s information security risks and assess their impact on the operations across your business.

Stay up-to-date
Create a real-time view of cybersecurity threats and vulnerabilities, ensuring that your always maintain just the right level of security.

Stay Compliant
Integrate information security risk management into your organisation’s cybersecurity management system, keeping compliance and improvement at the heart of everything that you do.

Proactively reduce your risks
Define and monitor how to mitigate risks in your business, ensuring cyber security remains under control, and in constant oversight.

Track your progress
Monitor your risk management measures and systematically report on your business’s information security situation.

Clarity at every step
Include low-threshold reporting of security and data protection incidents, for a full view of everything you need to manage your audit plans.
Book a call with our experts
Tell us about your information security risks or let us guide you in a demo.

