Pinpoint weak points in your IT infrastructure, systems and processes and sure compliance to the DORA regulations.
The EU’s DORA Regulation applies to organisations that handle financial services, such as banks, insurance companies, and investment firms. The goal of DORA is to strengthen the Cyber Security of financial institutions, ensuring that the sector remains resilient to serious operational disruptions.
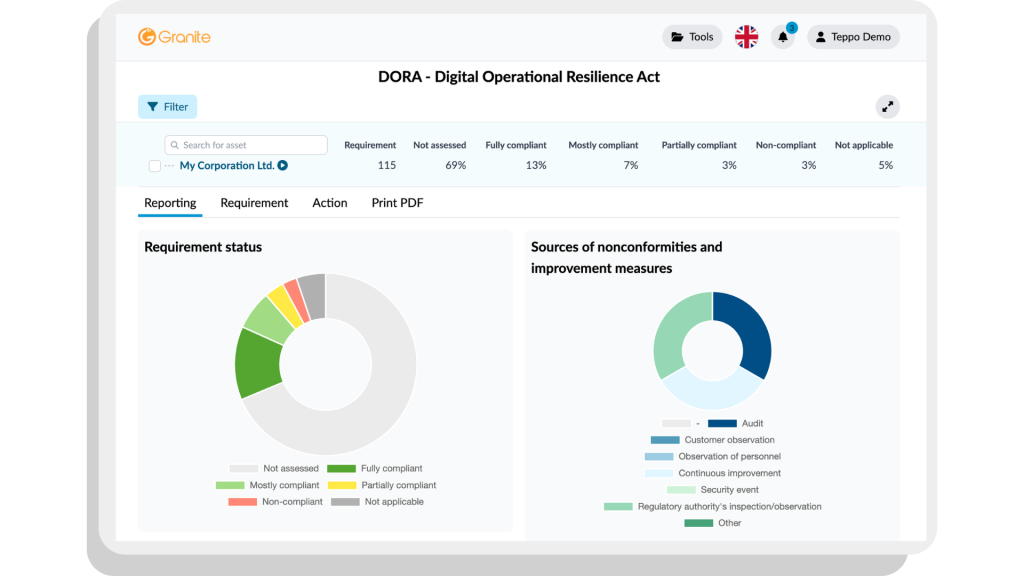
Granite’s DORA Security Requirements Tool is designed to comprehensively support organisations in managing cyber security risks, achieving compliance, and continuously improving cyber security.
With our tool, organisations can assess the maturity of their cyber security measures, create action plans, and verify compliance with the DORA Regulation.
Granite’s DORA Security Requirements tool helps you ensure that your organisation not only meets requirements, but also elevates your cyber security practices, protecting your most valuable information assets and your business continuity.

Evaluate the current state of your organisation's cyber security and identify areas for improvement. Utilize a consistent assessment model that provides a clear understanding of the maturity of the organisation's cyber security practices.

Document your processes in a high-quality and real-time way, to ensure that compliance is always at your finger-tips, and that you are ready and prepared for risks at any time.

Develop cyber security through a continuous management model that extends throughout the organisation. Define clear responsibilities and ensure cyber security is part of daily operations.

Ensure that every step of your action plan contributes to the continuous improvement of your cyber security and compliance. Granite’s tool makes it easy to build your action plans and monitor their successful delivery.

Monitor how you implement cyber security measures and the status of all of your requirements by using a guided assessment model. Report regularly on progress and make necessary updates to controls in real time.

Combine tools for the most comprehensive tool kit you can get, including information risk management, incident management and ISO/IEC 27001 compliance.
Let us show you around, or join us for a chat.
