Granite’s tools have you covered for all of your cyber security, data protection and IT compliance goals. Identifying and evaluating information security threats has never been so straightforward, letting you standardise, automate and monitor your process and report it all effectively.

Information security management is essential to ensuring business continuity, since the threats are wide and impactful. Granite helps you get proactive about identifying weaknesses and getting systematic about evaluating and monitoring improvements. IT security must be integrated into daily operations to ensure your strategic goals are being met.
With Granite’s It Risks & Compliance tools, you ensure that your organisation’s information security management is systematic and transparent.
Our tools support you to not only identify but prioritise risks to your business, and implement plans of action to reduce or remove these risks. Automated monitoring and reporting allows you to have real-time data at your fingertips, meaning decision making is simpler and audit reporting quicker.
Granite meets all external requirements and helps you to raise your standards internally. We improve the IT security culture in -house, raising business continuity and stakeholder trust.
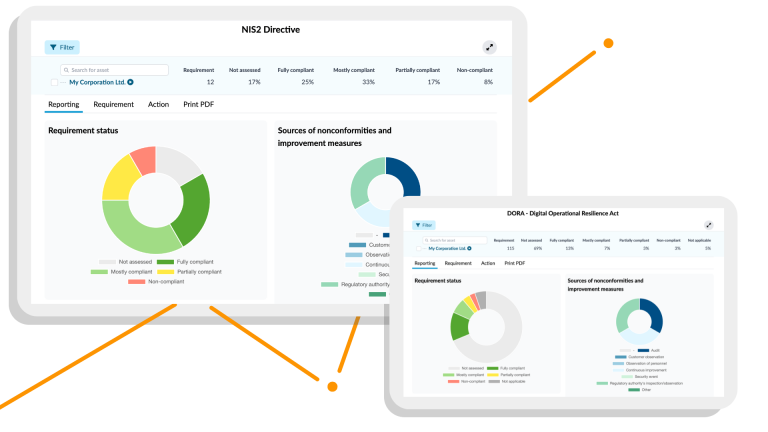
Assess the current state of information security, create an action plan, and demonstrate compliance with the NIS2 directive.
Evaluate critical points of your operating environment, locate development needs and ensure preconditions for the continuity of operations.
Manage compliance and documentation, assess the maturity level of your organisation, and address identified deviations and improvement targets. ISO/IEC 27001:2022.
Assess the current state of cyber security, create an action plan, and demonstrate compliance with the DORA Regulation.
Involve all employees in the development of information security with an incident reporting channel: receive, process, develop and report.
Identify and assess information security risks associated with your operations. Develop operating models for better security and reporting the results.
Maintain and manage your organisation's policies, rules, guidelines, and practices to ensure compliance and effective decision-making.
Identify, assess, and manage risks associated with personal data processing and ensure GDPR compliance with the Granite DPIA – Data Protection Impact Assessment tool.
We can do a short demo, set up a free trial, or simply discuss your needs.
